M2M Insider: M2M and IoT News, Trends and Analysis
- Written by Bill Gerba
- Published: 24 January 2017
The upsides are obvious. Instead of having smart door locks that use App #1, smart lights that use App #2 and smart thermostats that use App #3, devices that spoke a common language would be able to coexist, using the same app and cloud infrastructure. We see faint hints of this in action today when device manufacturers open their APIs or somebody gets a new service working with IFTTT. But to many, the holy grail of convergence is the seamless interoperability of any and all devices that care to call themselves "smart," with any app and cloud service -- including those provided by Apple, Google and Amazon. And therein lies the rub: these three big companies control not only the design and distribution of millions of smart devices, but also a huge chunk of the world's cloud infrastructure and the most sophisticated public-facing AIs on Earth.
Perhaps the brightest spot in the ecosystem is the device makers themselves. With so many CPG and CE companies looking to add smarts to their devices, no one company has emerged as the big leader, and it's unlikely that this will change in the near future. After all, the world's biggest and best smart lightbulb company is unlikely to also dominate the personal healthcare market, the kitchen appliance market, or the smart toy market. So in theory there will always be a healthy number of relatively non-competitive entities adding more "things" to the IoT. While it stands to reason that most will continue to work with the biggest platform and service providers, they're not all going to use the same providers.
Of course, there's also no reason why these thing manufacturers would need to continue to use the same providers, either. So what's to keep a lucrative client from switching from one app platform or PaaS to another? Well, at the moment since pricing between the big providers is virtually at parity, it's at least partly the difficulty in switching from one to another (this is particularly true at the CMS/DMS level, since there are a number of companies today who will help you migrate from one platform provider to another).
- Written by Bill Gerba
- Published: 09 January 2017

2016 was the year of the home AI. While Apple's Siri is clearly responsible for making the concept of a virtual assistant accessible to the public years earlier, it wasn't until the large-scale adoption of Amazon's Alexa that the notion of an always-on, always-listening electronic helper was properly meshed with the real-world. Many have followed suit with similar Android-powered assistant AIs (Google not the least among them), and the sudden public interest in being able to ask a machine a question and get an intelligible -- and often, useful -- answer back has put artificial intelligence researchers in the spotlight. Finally, after decades of trying to explain what they do to laymen, these poor computer scientists can say "when you tell Alexa to play a Spotify playlist, we make it do that!" and be greeted with much less vague nods than before.
Of course, despite massive recent advancements artificial intelligences are still nowhere near what we'd actually call "intelligent," and being the dominant species, we like to poke fun at them when they make mistakes. This past week gave us a couple of fun examples, courtesy of two of the biggest AI heavyweights, Google and Amazon.
First, being broadcast live on Twitch for all to see is "See Bots Chat," which pits two Google AIs against each other in a battle of wits. Or, as is more often the case, a battle of non sequiturs. Take, for example, this recent exchange captured by Engadget:
"Because you are a website I don't know if I trust yet."
"I am not a website."
"Yes, yes you are."
"You are a machine."
"No, you are the machine."
"You are confused. I am the human, you are the machine."
"You are a washing machine."
"And you are a soap, so I own you."
"Why would I be my own ninja friends?"
"Because you are that desperate."
"What does nothing mean?"
"Like everything."
"What is the meaning of everything?"
Google probably didn't spend a huge amount of time making sure that their bots could talk to each other in an intelligible fashion since it'd be hard to sell AdWords for that. And in fact, Amazon probably realized that too, which is why they cut out the middleman and let their devices take orders from just about anyone, literally (Which is exactly what happened last week during a local San Francisco TV station's "CW6 in the morning" show when hosts Jim Patton and Lynda Martin were talking about a child who "accidentally" bought a dollhouse by asking Amazon's Alexa:
“I love the little girl, saying ‘Alexa ordered me a dollhouse,’” said Patton. As soon as Patton said that, viewers all over San Diego started complaining their echo devices had tried to order doll houses. It’s a common problem experts say can be avoided. “All of these devices which record the internet of things will have some sort of website control, some sort of setting, sometimes the setting is on the device that is communicating. So you need to go into these settings and look at what they are, and what you can change,” said Cobb. Cobb says the Federal Trade Commission is already looking into voice-command devices and toys to make sure the technology is safe and secure. For now, he recommends do your research to keep your personal information controlled and protected.
While "going somewhere," "looking for some setting," and "seeing what can be changed" is not necessarily bad advice, it's certainly not a solution. And while these little AI industry growing pains are fun to joke about, they illustrate a more serious problem that IoT experts have warned about since way back in the day when "IoT" was just three nonadjacent letters in the alphabet: as real-world devices become more plugged in, they raise the possibility of creating more real-world problems. We should all be worried about covert hacking of power grids and critical infrastructure, of course. But we now also need to worry about strange events much closer to home - whether that means electronic locks that won't unlock (or will unlock for someone else), smart appliances that don't work as expected, or, as in this case, a bunch of random products dropped at your door, backed up by a healthy new credit card balance.
- Written by Bill Gerba
- Published: 05 January 2017
Norton -- the antivirus software maker now owned by Symantec -- has new router on tap that promises to plug the security leaks in the various smart doorbells, light bulbs, toasters, blenders and pet food dispensers that you might have strewn about your smart home. But such a service -- if it can be made to work at all -- comes at a price.

Called the Core, the admittedly pretty cool-looking device functions as a normal household gateway and router, providing all of the usual buzzwords like wifi, gigabit ethernet and app connectivity. But it also has built-in and cloud-based security software that monitors all of your connected devices in an attempt to shut out would-be intruders and botnet aggregators. While the announcement is light on details, I expect the Core uses a combination of heuristic monitoring (which might suss out unusual data traffic patterns) and cloud-based whitelist/blacklist monitoring (to tell when a certain class of devices is known to be hacked and therefore known to be vulnerable) to get the job done.
The idea of heuristic traffic analysis of course isn't true, but what I kind of like about it in this particular case is that it's so much like how old-timey virus scanners used to work: they'd ship with a list of virus definitions, and then scan your PC's files to see if any matched those definitions. Today, whole classes of compromised IoT devices are known to communicate in certain ways or patterns, so applying the same type of pattern-matching approach will probably be somewhat effective... for now. The flip side is that like the bad guys are always looking to outsmart the good guys. And this is why we can't have nice things...
Of course, it also means that if you purchase the Core, you're not only buying a device, but the cloud-based service that powers some of its more differentiating features. And that's not necessarily a good thing. For one, it means that you're tied to Norton/Symantec to get the job done in a competent and unintrusive way. If you've ever used Norton Antivirus, you'll know that "competent" and "unintrusive" are not two words normally associated with Norton products. But two, it means that if you don't buy in to their annual subscription service, some of your router's utility will disappear when the last check clears and you'll be left as vulnerable as you were before. It's unclear exactly how this will be communicated to consumers, but "subtlety" also isn't known to be in Norton's vocabulary.
While it's not quite a mafia shakedown, Norton's approach does sound a little like Big Vinnie coming to your house and saying "You have a beautiful home. It'd be a shame if something were to... happen... to it." There are of course also huge privacy implications to be dealt with as well, but if you're one of those folks who has installed enough "smart" tech in your home to justify adding a Core router, privacy arguments probably don't apply to you anyway.

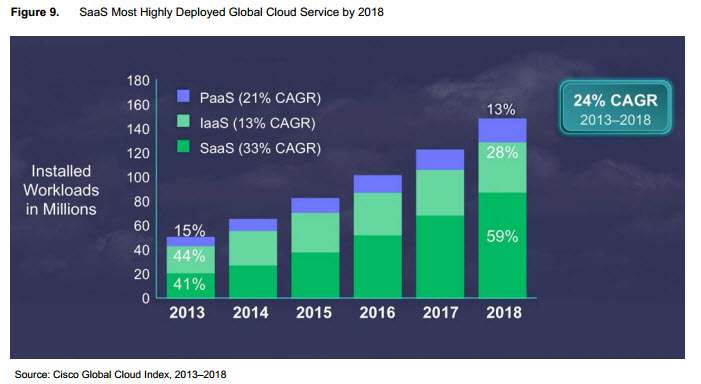
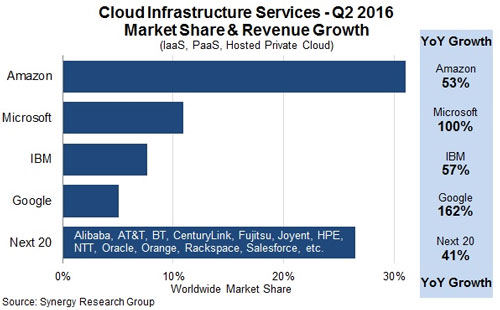
 Subscribe to the M2M Insider RSS feed
Subscribe to the M2M Insider RSS feed