M2M Insider: M2M and IoT News, Trends and Analysis
- Written by Bill Gerba
- Published: 19 August 2015
I don't generally trust most of the reports that comes out of the big research groups. Having been interviewed by numerous analysts over the past decade and a half, I know all too well how easy it is to get false information published, forever turning it into "fact." However, I do love the graphs, charts and infographics that the companies put out. Not because they're useful -- in fact, more often than not, they aren't. But they can be entertaining. To wit, Gartner just recently published their annual tech hype curve:
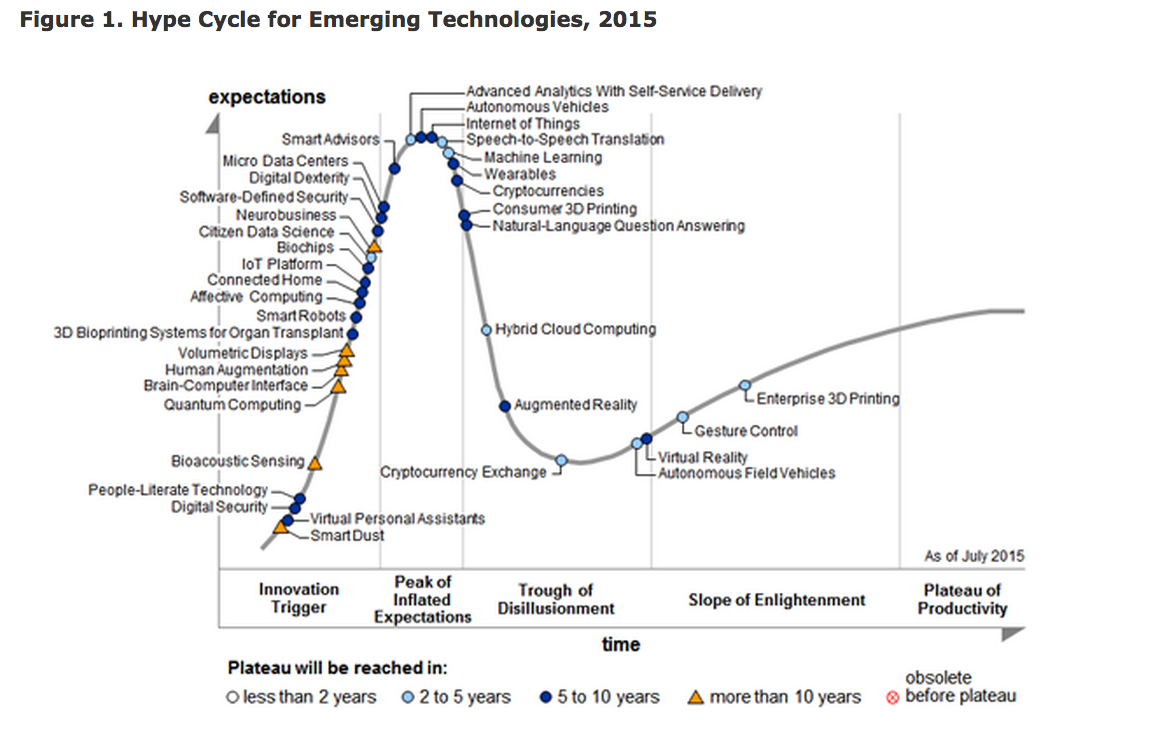
I've blogged on multiple versions of this curve over the years, mostly to point out how ridiculous some of their predictions have been. I thought this year's was interesting for a couple of reasons, not the least of which being that Gartner apparently thinks that IoT can't possibly be much more hyped than it already is.
To some extent, this makes sense. It's hard to imagine too many more news articles, conferences and breathless company press releases devoted to the Internet of Things, M2M, gee-whiz telemetry, smart cities, smart home, and just plain "smart." I personally think that the prediction is a bit off, and we still have a few years before we truly reach "peak hype" for the industry. However, that's the least of Gartner's transgressions when it comes to this chart.
While it's easy to dismiss "smart dust" and other far-off technologies that even Gartner agrees will take more than ten years to commercialize, tech that we have, see and use today ought to be better judged, and to me there are two big misses on this year's chart. First of all "machine learning" is up near peak-hype level and has yet to go through the "trough of disillusionment," which is frankly ridiculous. Do you use Siri? Google Now? Amazon Echo? Maps with live traffic? Major-retailer loyalty programs? If so, you're using machine learning, and in the past few years it has gotten pretty damned good. What's more, we hardly ever hear about it, because in its biggest and best implementations, it just works. It's mature, but still has lots of room for improvement.
On the flip side, Gartner pegs virtual reality as coming out of the trough and emerging a mature technology. This is, of course, total nonsense. If there's a more hyped consumer technology than VR, I can't think of it. And the tech demos we see from companies like Occulus and teased by Microsoft and others are just that -- demos. We're at least 5 years away from truly immersive hardware, and probably further than that out from considerable commercial adoption.
In all it's an exciting time to be in the tech business, and it's pretty clear that technology is going to continue to have a significant impact on the way we live work and play for decades to come. Some of the improvements on Gartner's hype curve have the potential to be truly disruptive. But even with all of the promise that IoT brings, I have to wonder whether it will ever live up to the hype.
- Written by Bill Gerba
- Published: 18 August 2015
The next phase of out-of-home advertising will start, ironically, in the home. At least that's the message that Amazon has been pushing with its bevy of always-on products that keep consumers connected to the Amazon marketplace 24/7. While the admittedly pretty cool Amazon Echo has gotten the lion's share of attention so far, the much less expensive (betwen free and $5) though not quite as useful Amazon Dash buttons are starting to gain some traction, and that of course means that it's time for the hacker community to jump on them.
Dash buttons are small, battery-powered wifi-enabled buttons that, when pressed, can automatically send an order request to the Amazon mothership. Run out of Tide detergent while doing your last load of laundrry? Just tap the dash button stuck to your washer and Amazon will get another bottle ready for you. About to stick the last razor cartridge onto your Gilette razor? Tap the branded button by your bathroom mirror and Amazon will put a pack in the mail. For forgetful people who already use Amazon, the system makes some sense, and for product manufacturers it's a veritable Godsend (if it works).
Of course, once you have a company like Amazon ponying up to give out little wifi-connected widgets for almost nothing, it's only a matter of time before some enterprising individuals come up with something more interesting to do with them than just buy more stuff, and now, that's exactly what has happened, as new dad Ted Benson outlined in a blog post on Medium:
every time a Dash button is pushed, it powers up its radio and promptly transmits the message, “Hi! My name is [MAC Address]!”
So, conceptually, problem solved. We just have to:
- Prevent the button from actually ordering anything
- Listen for Dash Button ARP probes, and
- Translate those probes into spreadsheet updates
The implementation he created is simplistic, but works, and one could imagine it being updated to allow for inputting different events by, for example, tapping the button several times in a row. I could also imagine changing things so that the button's message is different at different times of the day (e.g. saying "I woke up" when pressed in the morning, but "I went to sleep" when pressed in the evening).
I don't know if this violates Amazon's TOS for the Dash buttons, but if we're going to allow more brand intrusion into our homes, I think the least they can do is let one dad push a button on the wall so that a Google spreadsheet can be updated to let the world know that his child has pooped.
Is that really too much to ask?
- Written by Bill Gerba
- Published: 13 August 2015
Tesla, the hi-tech company that happens to make a few cars, recently found itself on the wrong end of an IoT hack that allowed attackers to remotely control certain aspects of its electric cars.

Considering that Tesla and founder Elon Musk are both high-profile targets, and considering that every vehicle they ship has a dedicated cellular backhaul connection that is known to be able to control every aspect of the car, it's not surprising in the least that hackers (good and bad alike) are targeting the platform. And in fact they've faced this problem before (for example, back in April 2014 when it was found that the doors could be unlocked remotely by an attacker).
But the attack put forward at the 2015 Defcon security conference highlights both the strengths and weaknesses of the current platform's security strategy:
They hit many dead ends — the report notes 90% of their presentation was dedicated to the walls they ran into — until finding a mysterious Ethernet port that they used to access the car's network which allowed them to connect to Tesla's virtual private network (VPN).
With physical VPN access, the hackers downloaded and decompiled the car's firmware, pointing them in the direction of an insecure folder of passwords. The hackers then spoofed the Wi-Fi network at Tesla service centers (which the car is automatically designed to connect), giving them access to a piece of software called QtCarVehicle, which controls all the vehicle's functions.
So while this particular attack is somewhat impractical, it does point out that even the most secure and technically adept IoT companies may find themselves in the security hot seat, particularly as their devices gain traction in the marketplace (hackers love juicy targets). Tesla, to their credit, has already put together an OTA patch for the flaw, and has introduced a bug bounty program that encourages other security researchers to find and disclose flaws in their software. That's certainly a far cry from what most automakers have done so far.

 Subscribe to the M2M Insider RSS feed
Subscribe to the M2M Insider RSS feed